🛡️ the Basics of Blockchain and Security Essentials
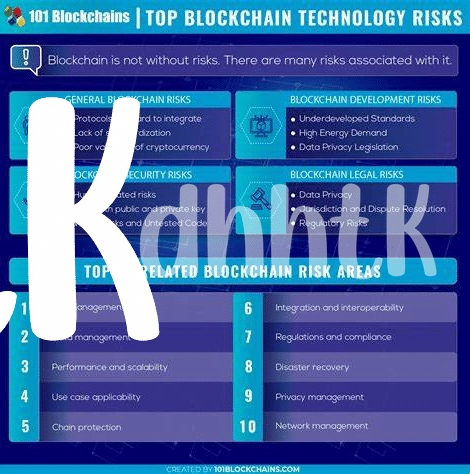
Let’s start by diving into a digital wonderland where trust is built not on promises but on mathematics and clever code – welcome to blockchain! Imagine blockchain as a digital ledger, a bit like a diary that’s not kept under your pillow but instead shared across thousands of computers around the world. Each entry in this diary is called a block, and every block is connected, creating a chain (hence the name, blockchain). Now, for the security part – it’s like each block is locked away in a clear safe; you can see what’s inside, but can’t tamper with it without everyone noticing. This is because each block contains unique codes that link it to the previous one, forming an unbreakable chain of blocks. If someone tries to mess with one block, they’d have to change every block after it, which is practically impossible given the computing power needed. Still, no kingdom is without its vulnerabilities, and that’s true for blockchain too. Here’s a quick look at its fortifications and the sneaky threats they face:
| Security Fortification | Description |
|---|---|
| Decentralized Network | Spread across many computers, making it hard to tamper with. |
| Cryptography | Locks each block with a unique code, linking it securely to the chain. |
| Transparency | Everyone can see transactions, which adds a layer of honesty. |
| Consensus Models | Requires agreement from multiple parties to validate transactions. |
Understanding blockchain and its security essentials is like learning the rules of a new board game; once you get the hang of it, you begin to see the strategy behind the game, as well as the potential pitfalls.
🔓 Unpacking the Risk: the 51% Attack Explained
Imagine if more than half the security guards at a bank decided to team up and rob it. Pretty unsettling, right? That’s a bit like a 51% attack in the world of blockchain, where someone controls over half of the computing power in a network. This gives them the unfair advantage to mess with transactions – like stopping them from happening or even reversing transactions to double-spend coins. While it sounds like a plot from a cyber-thriller, it’s a real risk, especially for smaller, less secure networks. It’s like having the keys to the vault as well as the security tapes, making wrongdoing tempting for those with enough computing horsepower. But don’t worry too much – bigger blockchains, like Bitcoin, are like Fort Knox; breaking in would require an unimaginable amount of computing power. Still, it highlights why diversifying and staying informed is crucial in the digital currency world. To dig deeper into how blockchain technology can safeguard against various threats, including those not visible on the surface, check out this insightful piece on https://wikicrypto.news/navigating-privacy-blockchains-solution-to-digital-identity-challenges. It’s a treasure trove of knowledge, offering a closer look at how smart contracts in e-commerce transactions are reshaping our approach to online security and privacy.
🎣 Phishing Attacks: the Crypto Con You Should Spot
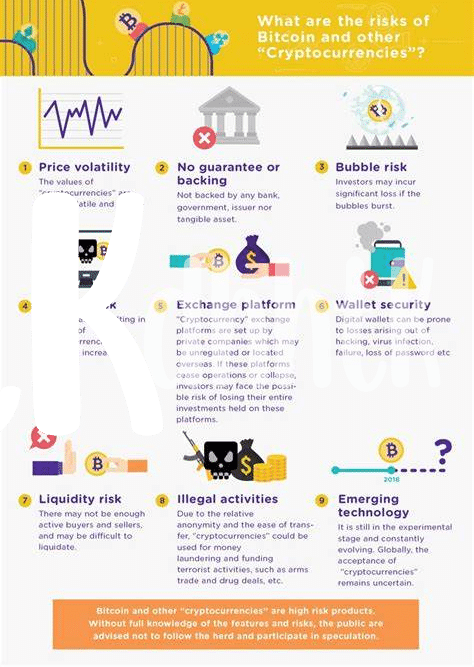
In the world of digital currency, con artists have a trick up their sleeve known as phishing. Imagine someone pretending to be a trusted person or company, sending you messages or emails. They’re fishing for your personal information, like the key to your digital wallet. 🚨 It’s like someone trying to sneak a peek at your secret diary – except, in this case, your diary is full of digital coins. These sneaky tactics can lead you to unknowingly hand over access to your cryptocurrency, thinking you’re making it more secure or helping out a friend in need. But just like you wouldn’t give a stranger your house keys, it’s crucial to guard your digital keys with the same caution. 🔑 Being aware of these cons and questioning anything that looks suspicious are your shields against these digital pickpockets. Remember, in the vast sea of the internet, staying vigilant is the key to keeping your digital treasures safe. 🛡️
🐛 Smart Contract Bugs: a Hidden Danger Lurking
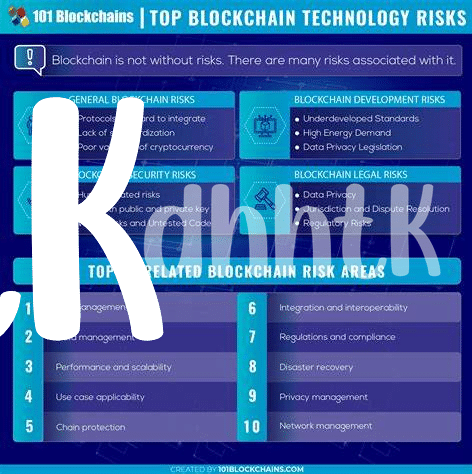
Imagine diving into a pool, expecting it to be full, but instead, you find out too late that it’s surprisingly shallow. That’s kind of what happens when we talk about the hidden dangers lurking within smart contracts. These are like the rules or agreements you set up when you do things with cryptocurrencies, except they automatically do what they’re supposed to when certain conditions are met, no human interference needed. Sounds cool, right? But here’s the tickle: just like any computer program, these contracts can have bugs or mistakes in their code. And in the world of crypto, such bugs aren’t just a nuisance; they can be an open invitation for troublemakers looking to swipe your digital coins. It’s similar to leaving your car unlocked with the keys in the ignition. By understanding how important it is to check and double-check these contracts, we can help safeguard our digital valuables from those looking to take advantage. If you’re curious about how this ties into the bigger picture, like how bitcoin in e-commerce and the blockchain evolves, knowing about these risks is crucial. So, it’s not just about keeping your own coins safe; it’s about ensuring the whole system remains trustworthy and reliable for everyone.
🔄 the Double-spending Problem: Why It’s a Threat
Imagine you’re at a market, and you pay with a $10 bill for an apple. Now, imagine if you could somehow use that same $10 bill to buy another apple, without the first seller realizing. That’s essentially what the double-spending problem is about in the digital world of cryptocurrency. It’s a sneaky trick some try to pull off, paying twice with the same digital coin. This threat is fundamental because it shakes the very foundation of trust in transactions. If double-spending were easy, confidence in digital currencies would plummet. Thankfully, sophisticated measures are in place to prevent this, but the risk isn’t zero. Recognizing this threat is crucial for anyone stepping into the digital currency space, ensuring they understand not just the opportunities but also the vulnerabilities that come with it.
| Threat | Description | Impact |
|---|---|---|
| Double-spending | A fraudulent technique of using the same digital currency more than once. | Undermines trust in digital transactions and the integrity of the currency. |
🕵️♂️ Privacy Leaks: Understanding the Unexpected Risks

When we dive into the world of blockchain, we often celebrate its strengths, like security and transparency. But there’s a lesser-known side that could affect your digital safety – privacy leaks. Imagine, every time you make a transaction or participate in the blockchain, you’re leaving digital footprints. These aren’t just random marks in the digital world; they’re valuable clues that, if pieced together by the wrong hands, can reveal more about you than you’d like. It’s like unwittingly dropping crumbs that lead straight to your personal information. The challenge here isn’t just about keeping your data safe from prying eyes; it’s about understanding that in the blockchain, every transaction is a public act. This openness can sometimes work against us, especially when it’s not just human eyes we’re dealing with, but also sophisticated algorithms designed to analyze patterns and extract data. For more insights on protecting your digital identity and understanding the interplay between bitcoin and digital identity in the blockchain, it’s crucial to stay informed and cautious.
